Let's Encrypt
Let's Encrypt is a global certificate authority (CA) . It enables people and organizations around the world to obtain, renew, and manage SSL/TLS certificates. Certificates from Let's Encrypt can be used by websites to enable secure HTTPS connections.
Installation
From git
For using the service, it is preferable to use the Certbot client.
In Debian, there is the certbot package that can be installed, but you can also use the latest version from git:
cd /opt
if the git package is not installed, we install it:
apt install git
git clone https://github.com/certbot/certbot /opt/certbot
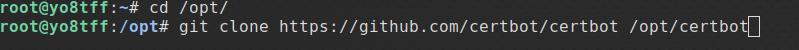
after cloning, we enter the certbot directory:
cd certboot
where do we launch the command to obtain the certificates:
./letsencrypt-auto certonly --standalone -d yo8tff.ro -d www.yo8tff.ro -d yo8tff.hamradio.ro -d florintanasa.sytes.net
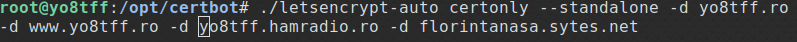
Attention: we will need to register after launching the command above and agree to the license.
if the response is like the one below:

we will need to stop the apache service or any other application that is occupying port 80:
systemctl stop apache2
and resume the command to obtain the certificate:
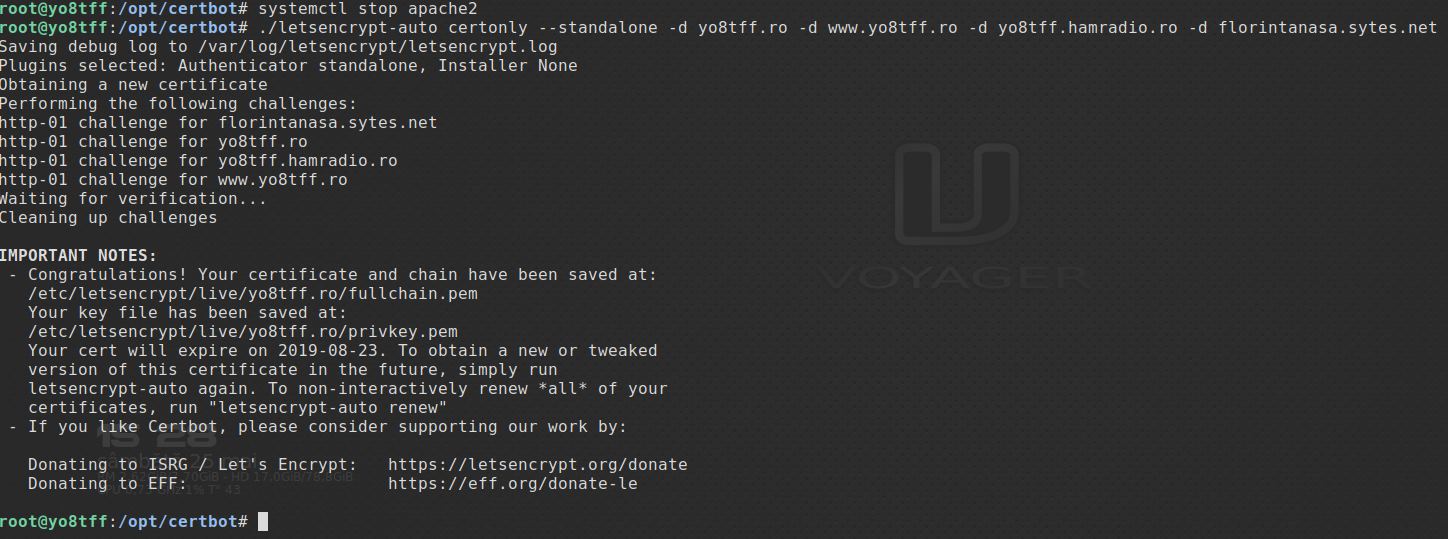
if a screen like the one above is obtained then the command has been executed successfully and we have the keys in the directory live/etc/letsencrypt/live/domain_name:
ls /etc/letsencrypt/live/yo8tff.ro/
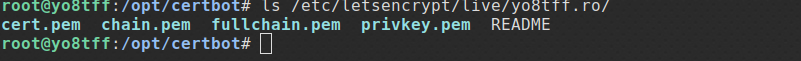
The keys above can be used for encrypting communications for services: apache, tomcat, etc.
Attention: Certification expires in 90 days
We can refresh the keys using the command:
/opt/certbot/letsencrypt-auto renew
To run the command automatically, for example on the 1st day of each month, we can use the crontab service:
crontab -e
0 0 1 * * letsencrypt-auto renew
Pay attention to the PATH variable, it must include /opt/certbot
we can see the commands that will be executed by crontab with:
crontab -l
A useful "guru" for crontab.
From the distribution packages in Ubuntu
Installation is easier for beginners.
To start, perform an update and upgrade.
apt update && apt upgrade

After that, we will install the certbot and python3-certbot-apache packages, the latter being necessary to automatically update the keys with the authority.
apt install certbot python3-certbot-apache

To obtain and automatically configure SSL for the Apache web server, Certbot needs to find the correct virtual host in the Apache configuration files (/etc/apache2/sites-available/domain.conf). The server's domain name will be taken from ServerName (ServerName domain) and ServerAlias (ServerAlias www.domain) defined within the virtual host configuration (/etc/apache2/sites-available/domain.conf).
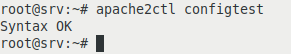
We check if the host or virtual host configuration file is set up correctly:
apache2ctl configtest
Attention before running the key request, it will be checked if ports 80 and 443 are open, from the local firewall or wherever it is located, and if the ports are forwarded in case we are behind a NAT (on some routers at the page - Virtual Server/port forwarding).
We run the key request:
certbot --apache

After entering a valid email and agreeing to the terms from Let's Encrypt, and if we subscribe with the email to the Electronic Frontier Foundation, here you can respond with N (No) but I responded with yes, we will need to indicate which of the hostnames (those written at ServerName and ServerAlias) we want to activate the keys and ssl connections for.
Attention - The names in ServerName and ServerAlias must be registered with a DNS service!
Since the keys are only valid for 90 days, for security reasons, we need to check if the key renewal service, which checks twice a day for keys that have less than 30 days of validity, is running:
systemctl status certbot.timer

We will check (simulating an update) if the automatic renewal service is functional:
certbot renew --dry-run
root@srv:~# certbot renew --dry-run
Saving debug log to /var/log/letsencrypt/letsencrypt.log
- - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - -
Processing /etc/letsencrypt/renewal/domeniu.conf
- - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - -
Account registered.
Simulating renewal of an existing certificate for domeniu
- - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - -
Congratulations, all simulated renewals succeeded:
/etc/letsencrypt/live/domeniu/fullchain.pem (success)
- - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - -Thus, from now on we will have updated keys and on time :)